Protect your Emails from
Advanced PHISHING, MALWARE & RANSOMWARE
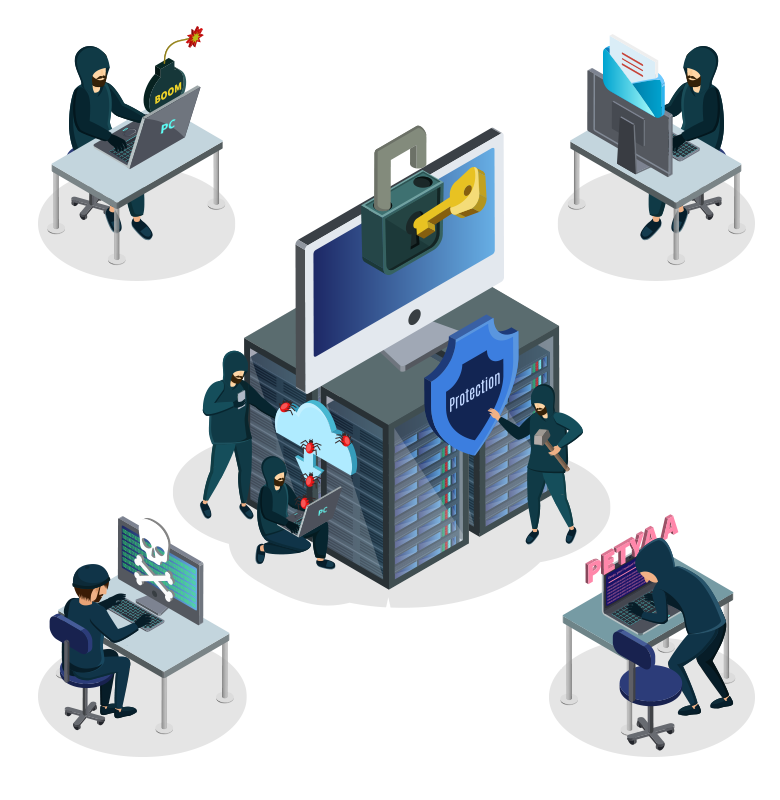
Phishing & Ransomware in Email, Web, and Others are the TOP cyber security issues that SorbSecurity aims to address at the fundamental level. Integrating with our robust API in SIEM will enable SorbSecurity to perform more tasks.

Securing With SorbSecurity
Productive & Customizable For CyberSecurity
The Truth of Attack is 99% starting with Phishing and Ransomware. Advanced security products to protect the customers and users from Email and Web, via phishing and ransom attacks.
- Phishing XDR
- Ransomware XDR
- SIEM XDR
Smart Notification
Never miss your fitness routine.
Proin massa odio amet tellus dignissim condimentum in viverra eget rhoncus, adipiscing eget ut donec vel enim, ultrices vestibulum nisl vel blandit dui enim hac sed a at laoreet eget sagittis dictum.
Anti-Phishing 365
Phishing is painful and 1st step to compromise your system. Our solution is to help you at here.
Anti-Malware 365
Losing files is terrible. We can help you identify the malicious easily.
SIEM EnPower
Cyber Intelligence and RestAPI Integration
SorbSecurity Cloud Email Security
Cloud-based Email Security Gateway Platform. We here defend the email threat for you where more than 90% attacks come from!
Solution Integration
More than a solution but partnership to streamline everything using Cloud-based API.
Security in Blockchain
Blockchain gives more security and privacy.
Do you fear a cyberattack?
What It Might Cost Your Company?
Any business can suffer catastrophic effects from cyberattacks, but small businesses are particularly vulnerable. Unprepared small businesses may have to deal with severe financial consequences as well as harm to their reputation, pricing strategy, productivity, employee morale, and other factors when a cyberattack occurs.




